
This tutorial provides step-by-step instructions on how to set up MTA-STS and TLS reporting with DMARCLY.
MTA-STS, short for Mail Transfer Agent - Strict Transport Security, is a technology that allows email servers to declare the ability to receive Transport Layer Security (TLS) connections and specify whether sending SMTP servers should refuse to deliver to email servers that do not implement TLS with a trusted server certificate.
A man-in-the-middle (MiTM) attack is a cyberattack where the attacker secretly intercepts the messages between two parties and possibly alter them. Attackers can use MiTM attacks to steal sensitive information like login credentials, bank accounts, or corrupt data, by relaying traffic between the sender and the receiver.
STARTTLS can be used to turn a plain text SMTP connection into an encrypted one whenever TLS is supported on the receiving server ("Opportunistic" TLS). However, it's still susceptible to MiTM attacks in that the STARTTLS command can be overwritten by the attacker, unnoticed by the receiving server.
With MTA-STS, a domain administrator can dictate that email servers that support MTA-STS will not send emails to their domain via an unencrypted connection. This makes MiTM attacks much harder to conduct.
In order to set up MTA-STS, first you need to create a TXT record on _mta-sts.your-domain to indicate that your domain supports MTA-STS:
_mta-sts.your-domain IN TXT "v=STSv1; >In the record value v=STSv1; > above:
You can log in to the dashboard, go to DNS Records/MTA-STS & TLS-RPT, and you will find such a record, as shown below:
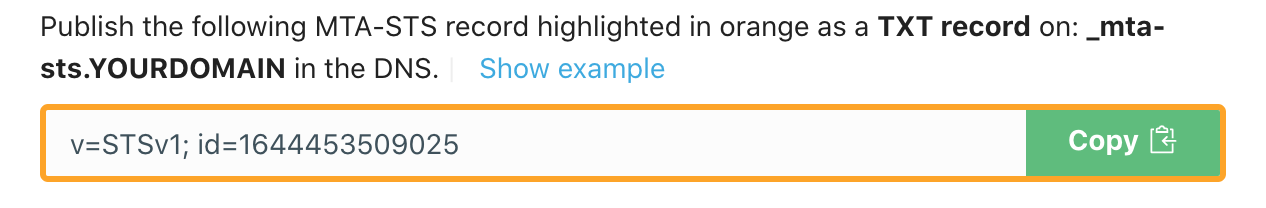
Simply click the green button as illustrated above to copy the record to the clipboard, then publish it in the DNS.
Next you need to create an MTA-STS policy as follows:
version: STSv1 mode: testing mx: your-email-host max_age: 86400In the policy above:
Modify the mx value in the MTA-STS policy based on your own MX settings. For example, if your domain's MX record points to: your-email-server.com , you need to update the policy to:
version: STSv1 mode: testing mx: your-email-server.com max_age: 86400If your domain has multiple MX records, create multiple mx key/value pairs in the policy:
version: STSv1 mode: testing mx: your-email-server.com mx: another-email-server.com max_age: 86400Once the policy looks good, save it in a txt file mta-sts.txt somewhere on your computer.
Next we need to host the MTA-STS policy file so that it becomes accessible for all on the internet at:
https://mta-sts.your-domain/.well-known/mta-sts.txtYou need to take the following 2 steps:
Once this is done, ensure the MTA-STS policy file is accessible by navigating to the following url in your favorite browser:
https://mta-sts.your-domain/.well-known/mta-sts.txtPlease make sure to set up the SSL certificate correctly on your web server, so that https://mta-sts.your-domain/.well-known/mta-sts.txt is accessible via HTTPS, not HTTP. Self-signed certificates won't work.
If you are able to see the policy in the browser without any SSL/TLS warning, the policy is probably correctly hosted.
Also, make sure the server returns an HTTP 200 status code from that url. That is, there must not be any redirect. The url in the browser is a good indicator of this. You should see the following url in Chrome once the page is loaded:
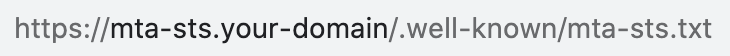

If your MTA-STS url contains a redirect, the MTA-STS checker will indicate the error:

Now that you have MTA-STS in place, you can implement TLS Reporting (TLS-RPT) to receive TLS aggregate reports. With TLS aggregate reports, you can identify email security issues and take action to fix them as necessary.
Setting up TLS reporting is a matter of publishing a TXT record on your domain as follows:
In the record value v=TLSRPTv1; rua=mailto:[email protected] above:
When you sign up with DMARCLY, a mailbox is created for you in our system to receive TLS reports. Log in to the dashboard, go to DNS Records/MTA-STS & TLS-RPT, and you will find the TLS-RPT record pointing to that mailbox, as shown below:
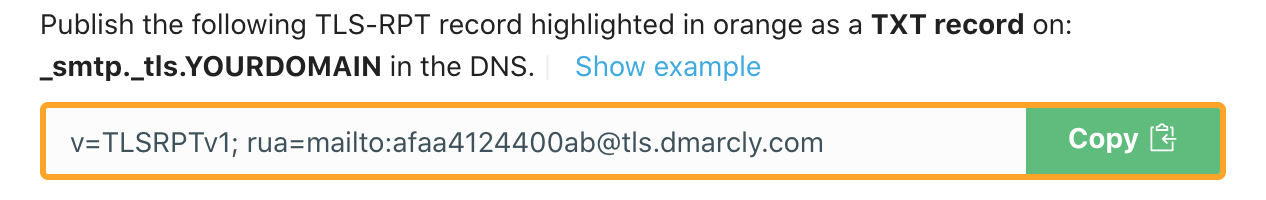
Keep in mind you will need to use the value shown in your dashboard, instead of the one in the screenshot above.
Once you've completed the above steps, you can use our free MTA-STS checker to make sure things are set up correctly.
After you have published the TLS record with the rua tag set to that mailbox, DMARCLY will start receiving TLS reports on your behalf. These reports are usually sent daily, therefore DMARCLY should have them ready a couple of days after you publish the TLS record.
Here is a TLS report example in JSON format:
< "organization-name":"Google Inc.", "date-range":< "start-datetime":"2021-05-20T00:00:00Z", "end-datetime":"2021-05-20T23:59:59Z" >, "contact-info":"[email protected]", "report-id":"2021-05-20T00:00:00Z_acme.com", "policies":[ < "policy":< "policy-type":"sts", "policy-string":[ "version: STSv1", "mode: testing", "mx: acme.com", "max_age: 86400" ], "policy-domain":"acme.com" >, "summary":< "total-successful-session-count":0, "total-failure-session-count":3 >, "failure-details":[ < "result-type":"validation-failure", "sending-mta-ip":"209.85.222.201", "receiving-ip":"173.212.201.41", "receiving-mx-hostname":"acme.com", "failed-session-count":2 >, < "result-type":"validation-failure", "sending-mta-ip":"209.85.208.176", "receiving-ip":"173.212.201.41", "receiving-mx-hostname":"acme.com", "failed-session-count":1 >] > ] >The following is what TLS report data looks like in the DMARCLY dashboard:
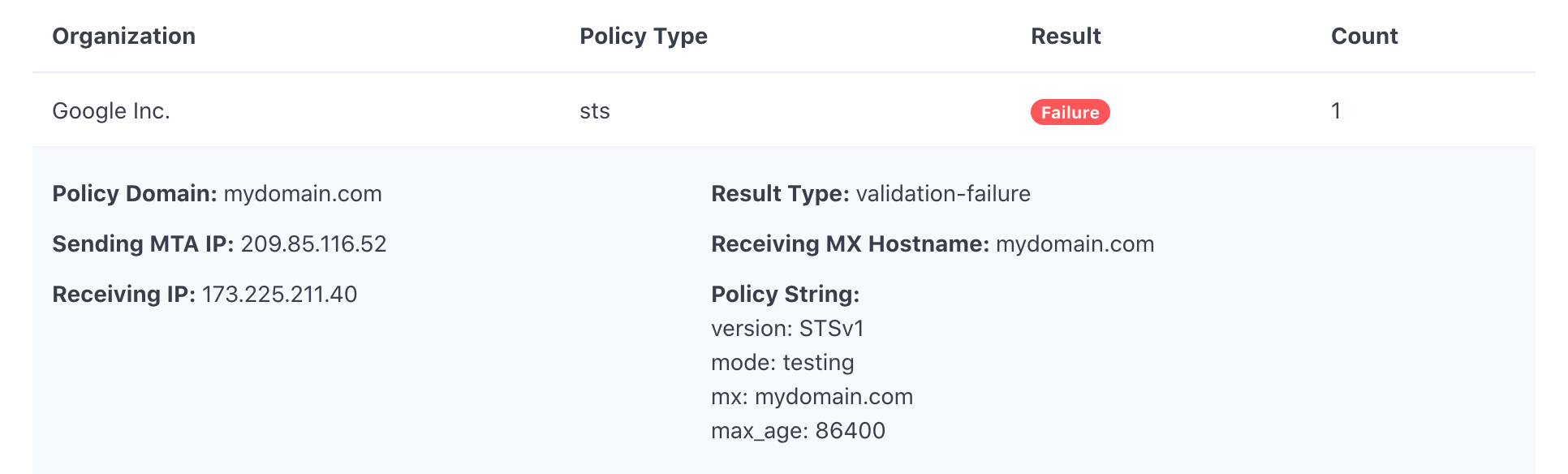
Get a 14 day trial. No credit card required.